 When writing about an analysis of the report on the Russian Hacking the other day, the following was mentioned …
When writing about an analysis of the report on the Russian Hacking the other day, the following was mentioned …
…What we’re seeing in this IP data is a wide range of countries and hosting providers. 15% of the IP addresses are Tor exit nodes. These exit nodes are used by anyone who wants to be anonymous online, including malicious actors.
That highlighted bit perhaps catches the eye.
What the heck is a TOR Exit Node?
OK, so let’s take this step by step.
The name TOR is in fact an acronym that stands for “The Onion Router”.
Every interconnected computer out there has a unique number called an IP address. When you connect to another computer, another IP destination, your IP address identifies you to that other computer. This is what happens when you surf the web, it is how it all works under the covers. If however you wish to be anonymous and hide who you are and where you are, then the Tor network offers a way of doing exactly that. The Tor Wikipedia page describes it like this …
Onion routing is implemented by encryption in the application layer of a communication protocol stack, nested like the layers of an onion. Tor encrypts the data, including the destination IP address, multiple times and sends it through a virtual circuit comprising successive, randomly selected Tor relays. Each relay decrypts a layer of encryption to reveal only the next relay in the circuit in order to pass the remaining encrypted data on to it. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing, or even knowing, the source IP address. Because the routing of the communication is partly concealed at every hop in the Tor circuit, this method eliminates any single point at which the communicating peers can be determined through network surveillance that relies upon knowing its source and destination.
That’s a lot of words to digest, so let’s try a series of picture.
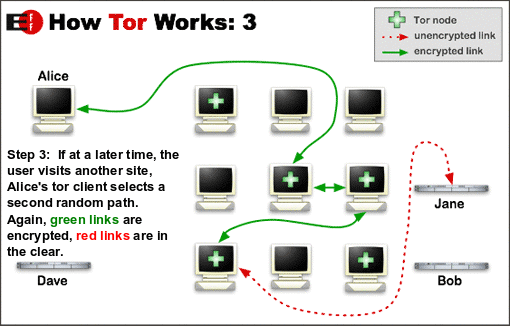
To answer the question, what both Jane and Bob see is a connection coming from a Tor exit node and they have no idea that the original connection was Alice and no way of finding out (well generally not, I’ll get to that). What is happening here is a series of onion like layers of encryption as data flows through this Tor router. Each node can only decrypt enough to enable it to send to the next node, and not where it came from. If you wanted to perform source identification, then you need to crack the encryption for a path of randomly selected nodes and that will be dynamic and constantly changing.
Not impossible, but it is dam hard to trace.
So what is Tor used for?
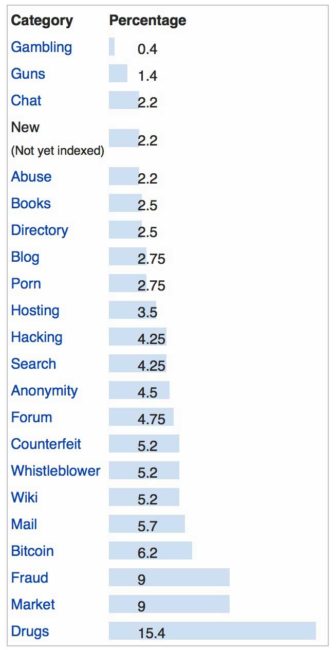
Rather obviously the motivation is to remain hidden and to also access the dark web and hidden services. Yes, some just want to remain anonymous, but to be frank, there is rather a lot of it is stuff you really do not want to ever get involved in. As of Jan 2015, the available “hidden services” break down as follows …
However, while the above breaks down the hidden services out there, don’t let the skew your thinking. About 40% of all the actual Tor traffic consists of ordinary people using bittorrent to download movies and TV shows. They just don’t want anybody complaining to their ISP that they are doing this.
If that is your thing then this is really not the best solution because you can be identified.
Is it truly anonymous, does it actually work?
No, it is crackable. For example …
The results presented in the bad apple attack research paper are based on an attack in the wild launched against the Tor network by the authors of the study. The attack targeted six exit nodes, lasted for 23 days, and revealed a total of 10,000 IP addresses of active Tor users. This study is particularly significant because it is the first documented attack designed to target P2P file-sharing applications on Tor.[101] BitTorrent may generate as much as 40% of all traffic on Tor.[102] Furthermore, the bad apple attack is effective against insecure use of any application over Tor, not just BitTorrent.[101]
It does of course crank up the degree of security, but do not be fooled into thinking it makes you 100% anonymous.
Tor Urban Legends
OK, a bit of fun. Like most things in life we tell stories to each other and so there are also Tor Urban Legends.
There are rumours of crowdfunded assassinations and hitmen for hire.
- Number of claims of this … well here is an example (towards the end, skip of the parts about buying tanks and missiles), and here is another example.
Is any of that actually real?
- Basically no. For example, here is an exposure of the scam here … and here is somebody who tried to engage (not really), and reveals that it was of course not real and was in fact a scam. It is basically a con job, they are simply after bitcoins. The beauty of it all is that when defrauded, then who exactly does the mark complain to?
Bottom Line
Yes, you can just download a Tor browser and start accessing the dark web, but you do need to be aware of a few specific things.
- It is not truly anonymous, those who need to crack the network and work out who you are can do so (For example Europol have cracked it, but will not say how because they want to continue doing so).
- On the Internet scams abound, but jump into the dark web and it is scams on steroids
Like the rather dodgy side of town where you really do not want to be at night, it is all best avoided if you want to stay safe.
Step one for somebody whose PC is infested with malware is … “OK, let’s start by getting rid of this Tor Browser you have here”.
As for Dave’s “malware” source, yes, if one is clueless enough to download executable code from a unverified TOR service,
you might get malware. If one stays away from that kind of risky behavior, one will likely fare better than with straight browsing-
TOR Browser has some extra functionality and safety built-in.
I’m not going to read the provided //Darkweb// link to “The Ecomomist”… Perhaps someone else can chime on that?
Actually, if you read the above article under “// TOR is pretty much your best option for privacy on the web //”
it seems like a good argument for using TOR…
NSA has apparently determined it works well enough to track as much as possible.
Now, is a good time for everyone to use TOR/TOR Browser, making anonymous browsing the new normal…
And, for “part 2”, (Again, read the article )
The ZMap tool is irrelevant for “regular”, privacy-minded TOR users.
Why would I care if someone identifies TOR bridges?
Most users won’t require a bridge.
Is this article a hit job?
Perhaps, not, but it is clearly slanted in a direction and has some glaring technical misrepresentations.
Citing the Economist as a reliable source classifies you.
Pointing out that I cited the economist classifies you.
Dave,
I use Tor for one main reason. To keep the data hoovers (adobe.tm, google-analytics, doubleclick, etc.) from tracking my normal browsing to add to their dossiers on innocent people like me. I run Tor in a firejail and usually without javascript. I just don’t want to be analyzed by surveillance capitalists.
By the way, like many Tor users, I do not do evil. Too bad Brin and Zuckerberg can’t say the same.
Your claim about europol “cracking” TOR is just funny and shows that you didn’t bothered to read much about the methods used to find out TOR users like pedophiles on the dark web. The bad apple attack mentioned in your article depend on an insecure application that reveals your real IP. Other methods work on exploits that can’t work on someone who have just disabled javascript on his TOR browser(you can easily do it with two clicks), or work by controlling both the entry node and exit node and analysing the traffic statistics over long period of time but it only works on specific scenarios were very few TOR users generated similar traffic but in most cases is simply not practical and only gets less practical as more people use TOR.
Europol doesn’t have a way to “crack” TOR, they have something like what I mentioned above that can only work on some specific scenarios just like the FBI and other similar organizations.
Why do you think they don’t want to tell about their method?, because it will only encourage a more safe useage in TOR like disabling javascript when you use some illegal website and they do need to disclose their methods if they want to put criminals in jail based on that method alone and when it is a pedophile who watch or upload child porn this can be the only proof they have.
“Step one for somebody whose PC is infested with malware is … “OK, let’s start by getting rid of this Tor Browser you have here”.”
Dude, a site that claims to value critical thinking, should, you know, think before writing.
Your bottom line makes TOR sound like it’s only for the dark web and that the browser itself is a main source of malware, both counts are outright wrong.
Let’s address your “It is not truly anonymous” fud.
TOR is pretty much your best option for privacy on the web; you dismiss it because it’s not 100% perfect? Unless you’re the target of Europol, worrying about their supposed crack is a moot point to bring up in the general use TOR discussion.
// main source of malware //
See here.
// Darkweb //
Tor has been described by The Economist, in relation to Bitcoin and Silk Road, as being “a dark corner of the web”
// TOR is pretty much your best option for privacy on the web //
Using TOR = waving a big bold flag that announces “target me” … https://daserste.ndr.de/panorama/aktuell/nsa230_page-1.html
// TOR is pretty much your best option for privacy on the web // … part II
Researchers from the University of Michigan developed a network scanner allowing identification of 86% of live Tor “bridges” with a single scan